Security Teams. See the Threats Hiding In Normal Traffic.
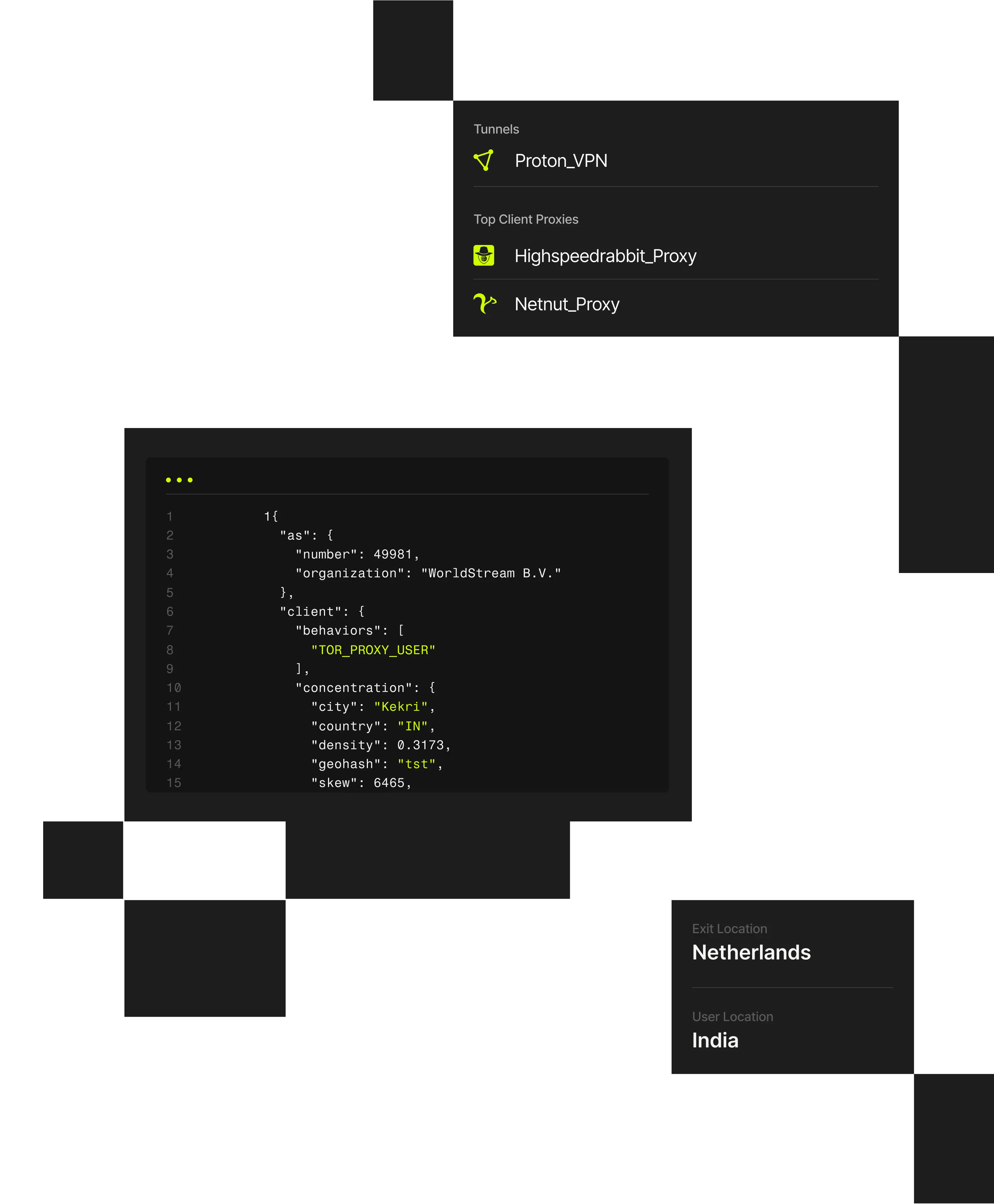
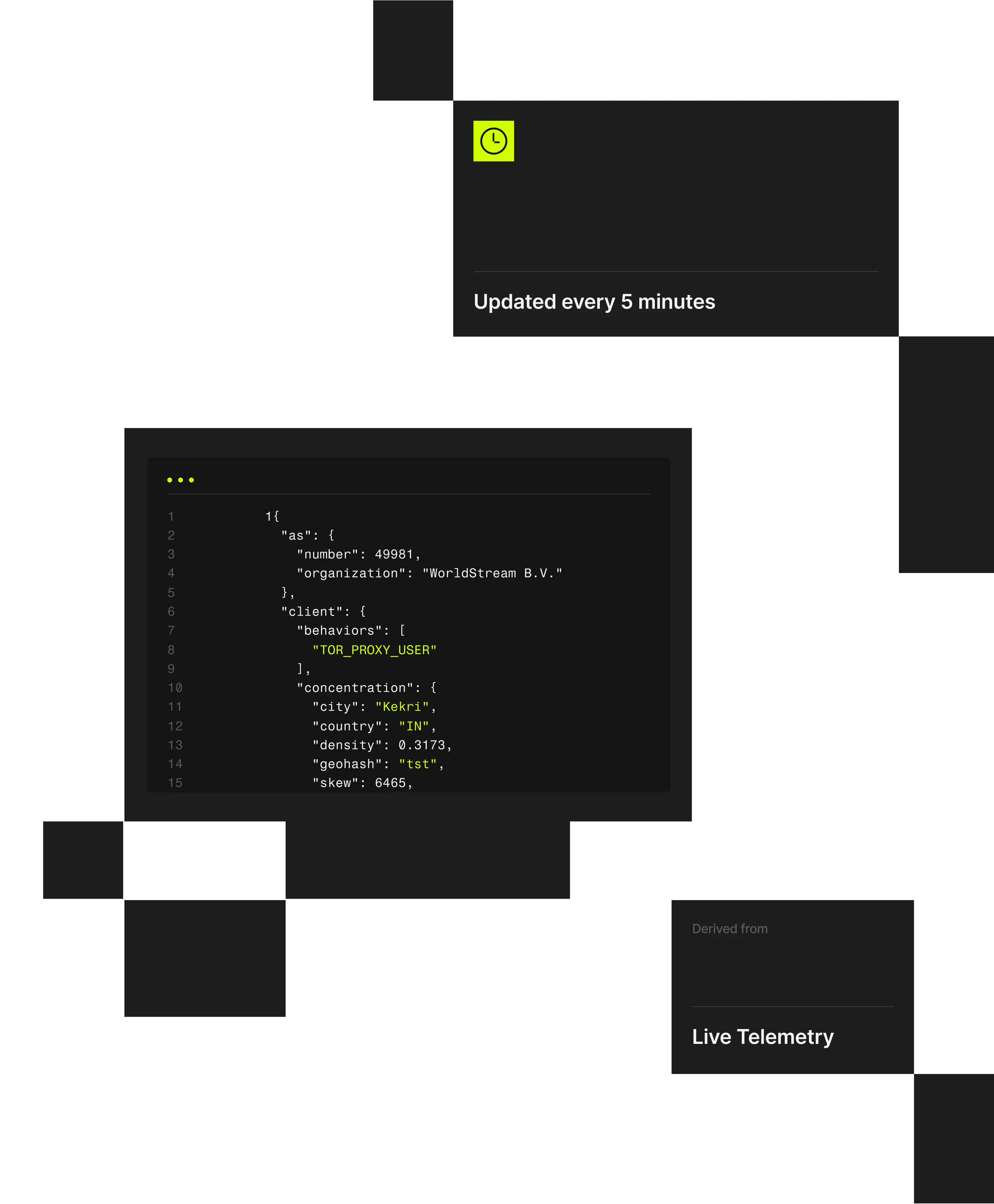
1 "client": {2 "city": "Weldon Springs"3 "behaviors": ["TOR_PROXY_USER"],4 "concentration": {5 "country": "US",6 "density": 0.202,7 "geohash": "9yz",8 "skew": 45,9 "state": "Missouri",
Security teams face attackers who rely on VPNs, residential proxies, and shared infrastructure to blend malicious activity into everyday traffic. Spur exposes the network context behind that activity, helping teams detect threats, investigate incidents, and enforce controls with confidence.


Threats Blend Into Legitimate Network Activity.
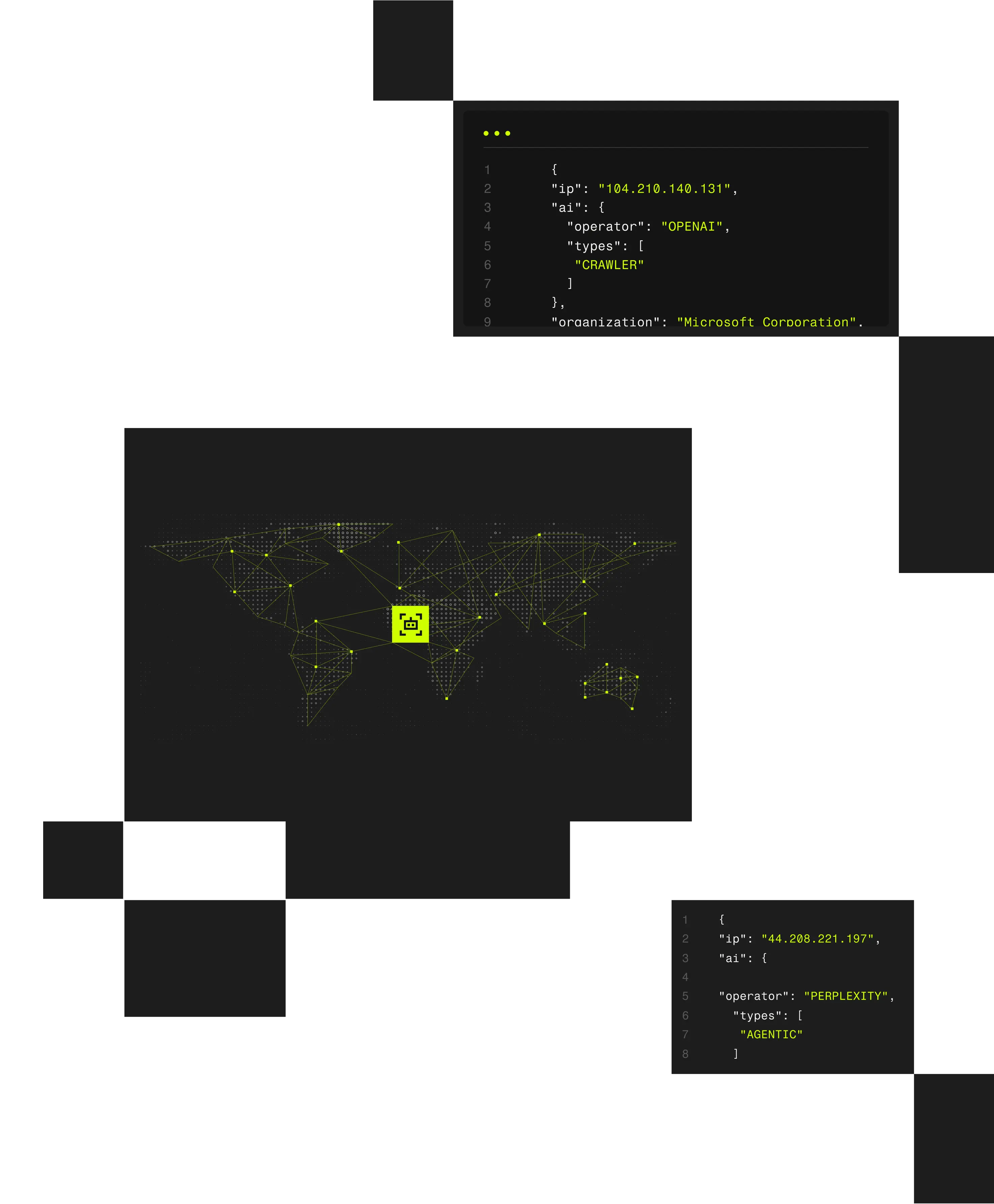
Modern security operations depend on logs, alerts, and telemetry that increasingly lack reliable network context. Attackers exploit anonymized infrastructure to mask reconnaissance, intrusion attempts, and lateral movement, making suspicious activity appear routine.
Without clear attribution, security teams struggle to correlate events, hunt threats, and enforce access controls effectively. Spur enriches security telemetry with high-fidelity infrastructure intelligence, enabling SOC and threat-hunting teams to spot hidden threats, correlate attacker activity, and respond faster.

Detect and Respond to Hidden Threats.
Spur delivers infrastructure-aware IP intelligence that helps security teams enrich telemetry, correlate attacker activity, and respond to threats that hide behind anonymized and shared network infrastructure.
Ecommerce Platform Strengthens Security Operations at the Edge
GoPuff improved visibility into inbound threats by identifying automated and anonymized traffic routed through residential proxies and shared infrastructure.
By enriching security telemetry with high-fidelity IP intelligence, the security team applied targeted controls at the perimeter, protected site availability during high-demand periods, and reduced noise from false positives without disrupting legitimate users.
Evidence You Can Act On.
Spur’s verified IP intelligence helps teams move faster, detect more, and protect what matters – without adding friction for real users.
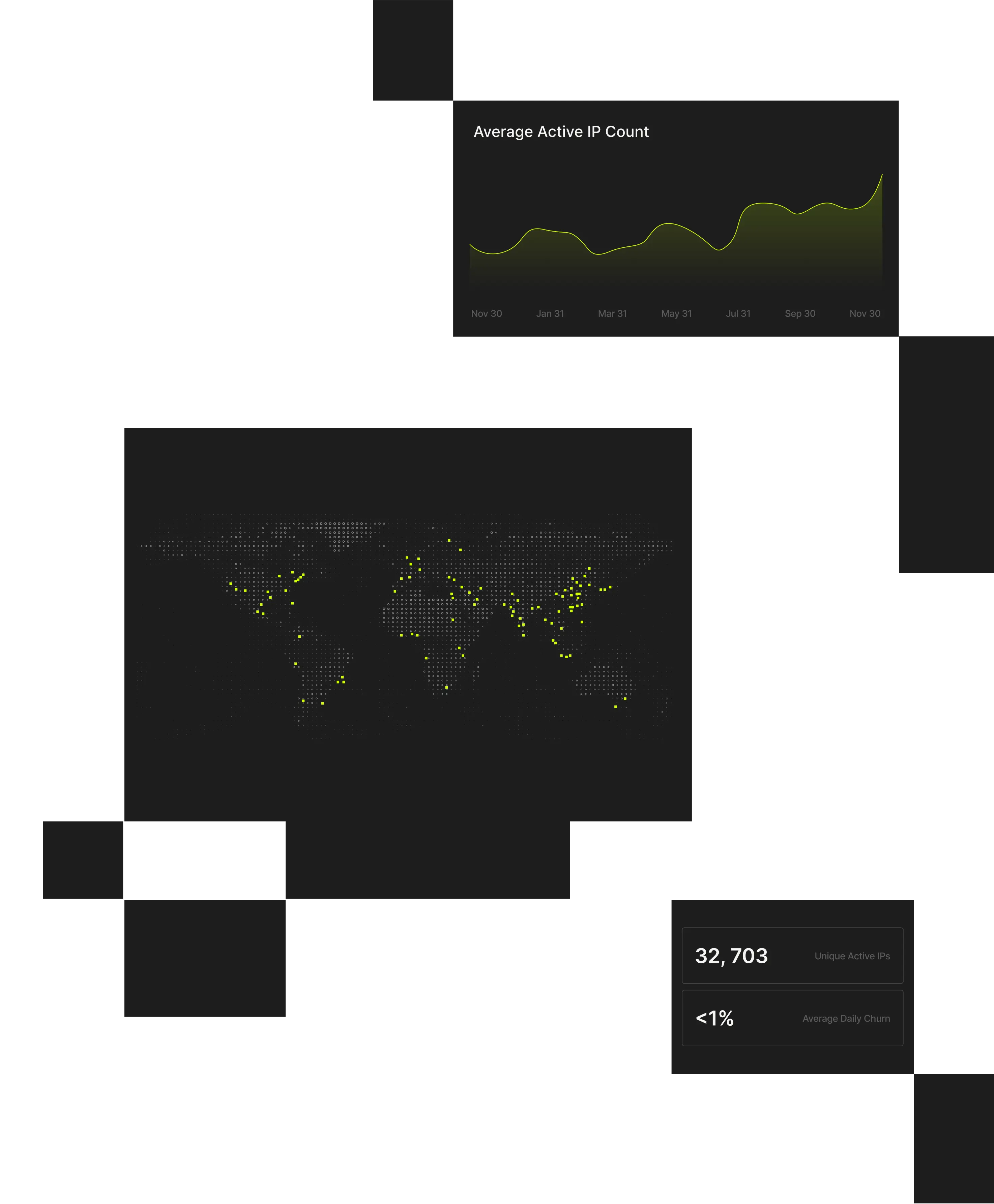
230M+
Unique anonymized IPs detected every 90 days, distilled into 60M suspect IPs daily
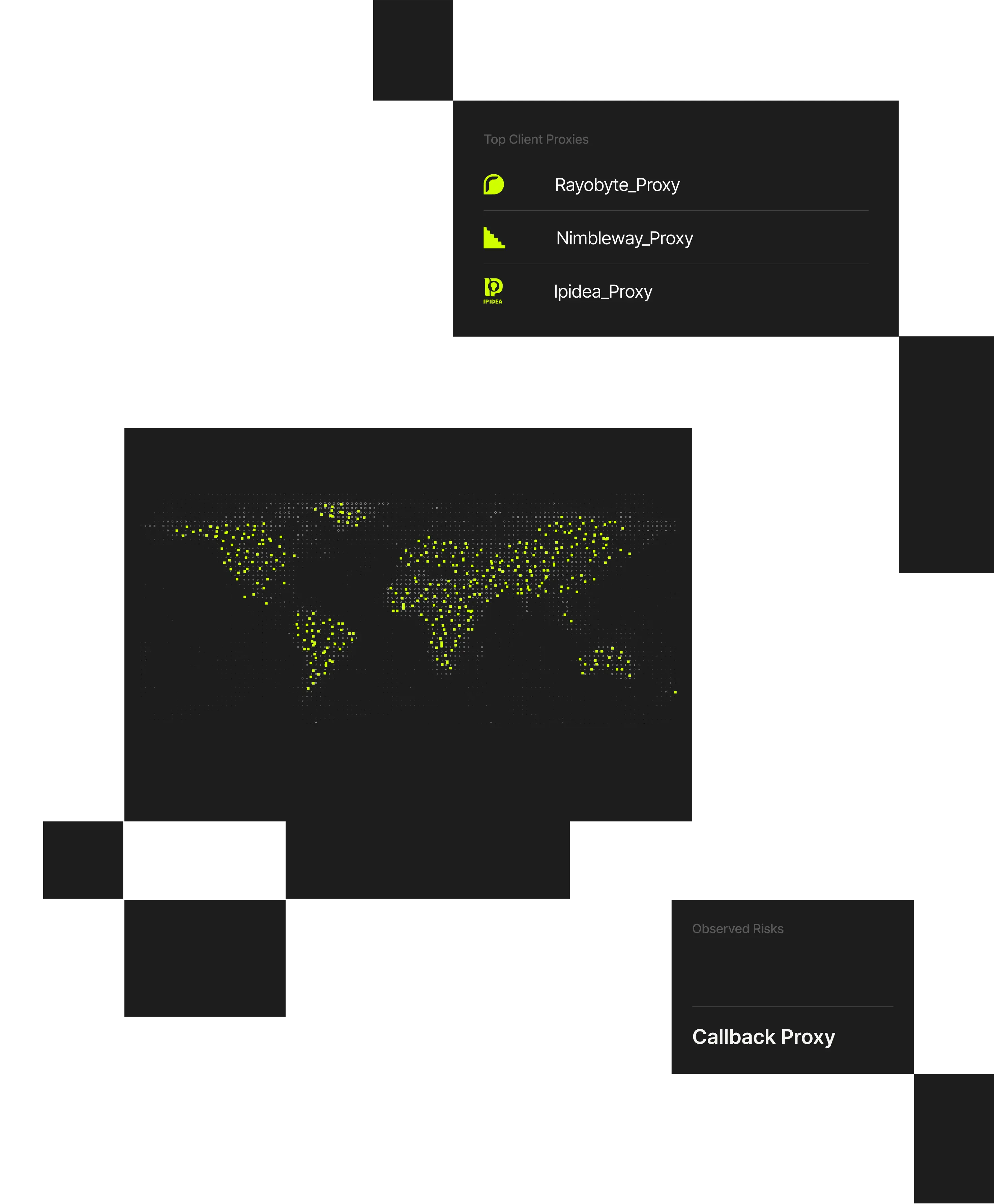
1000+
VPN and proxy services detected
20+
Enrichment attributes for full context (geo, ASN, proxy type, device, tunnel entry/exit, etc.)
Strengthen Every Team’s Visibility with Verified IP Intelligence.
Bring Clarity to Security Operations.
Detect anonymized threats, enrich security telemetry with network context, and accelerate investigation and response using Spur’s high-fidelity IP intelligence.