Discover Remote Worker Fraud. Expose Hidden Risk in Remote Hiring and Access.
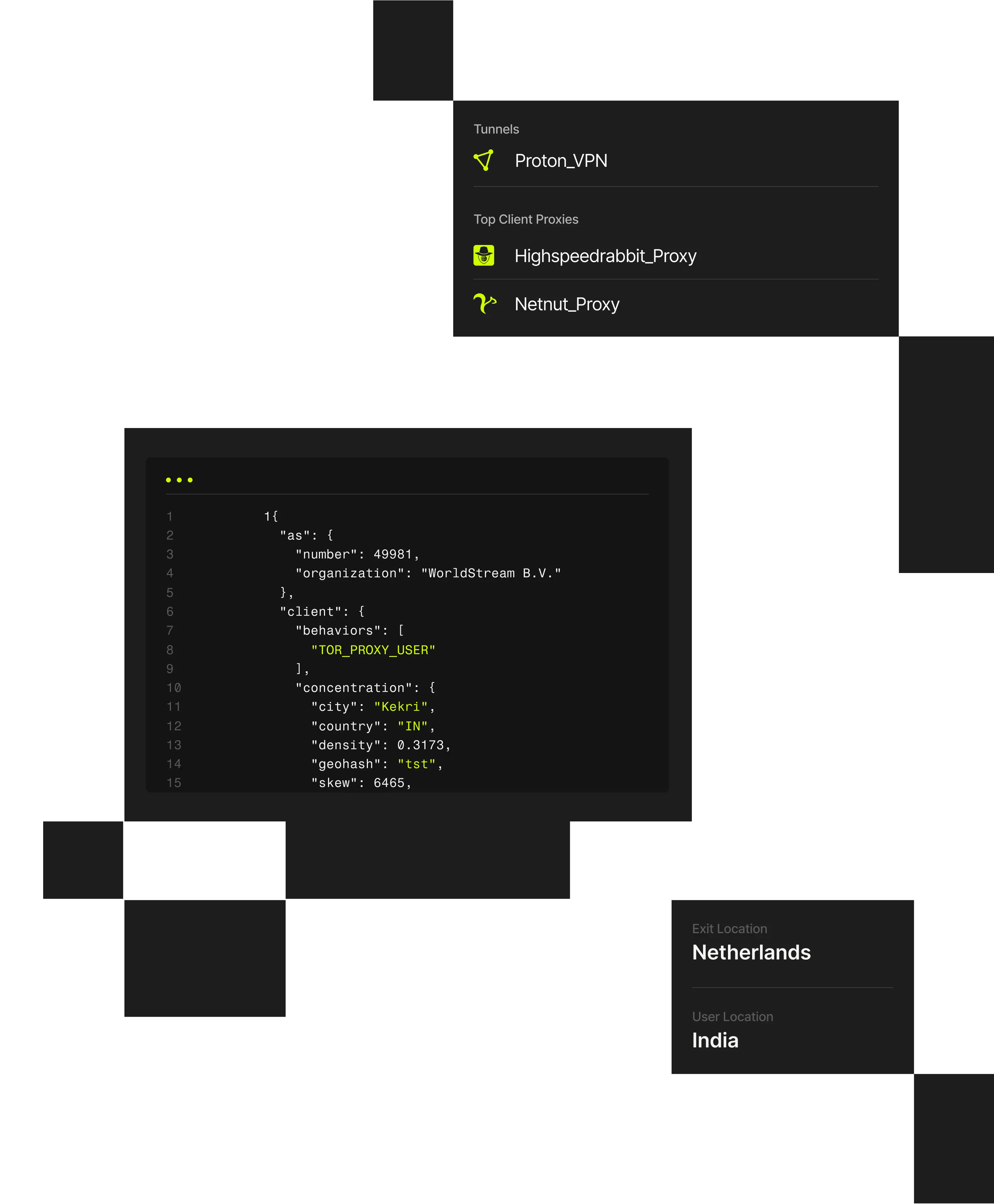
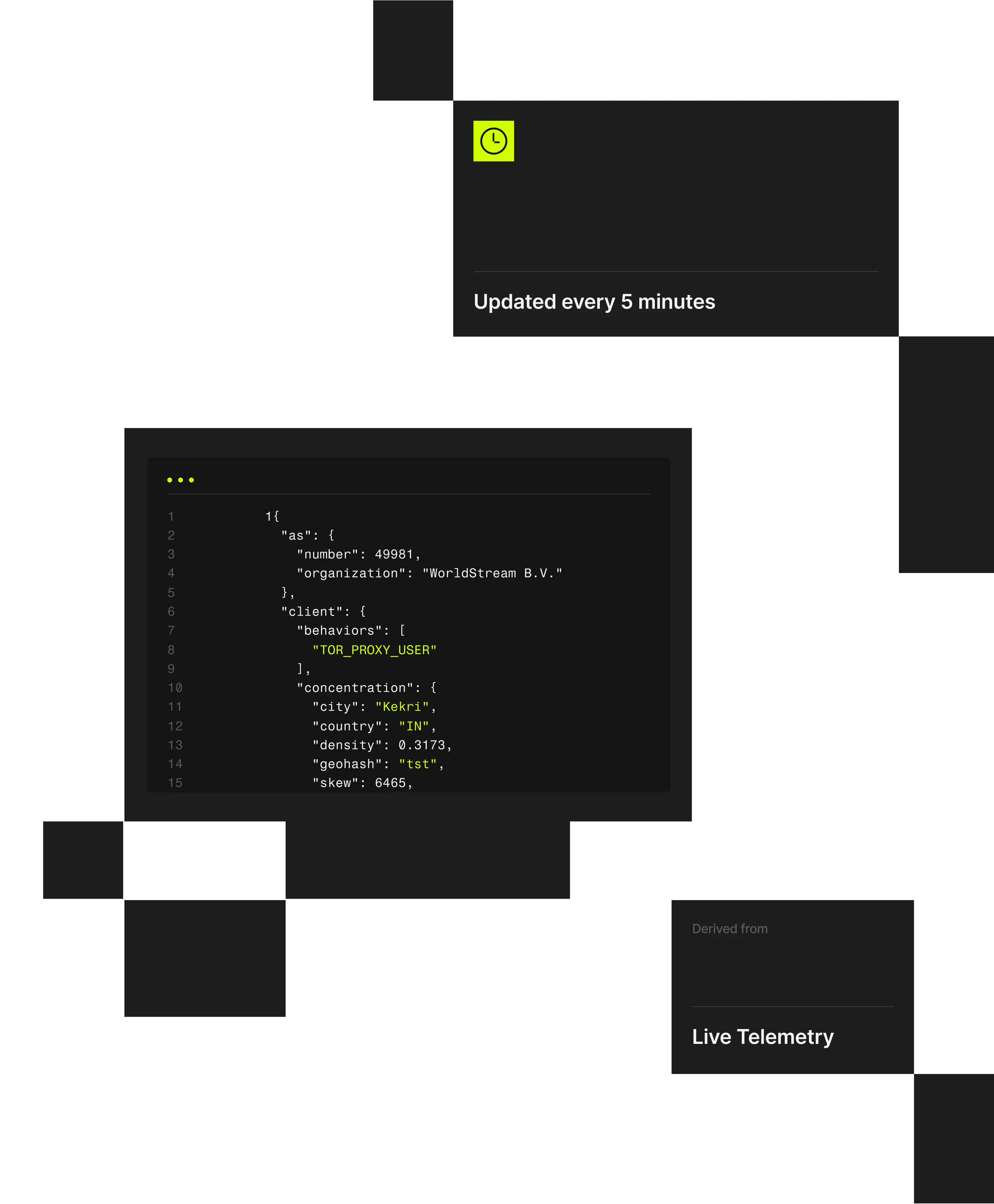
1 "client": {2 "city": "Weldon Springs"3 "behaviors": ["TOR_PROXY_USER"],4 "concentration": {5 "country": "US",6 "density": 0.202,7 "geohash": "9yz",8 "skew": 45,9 "state": "Missouri",
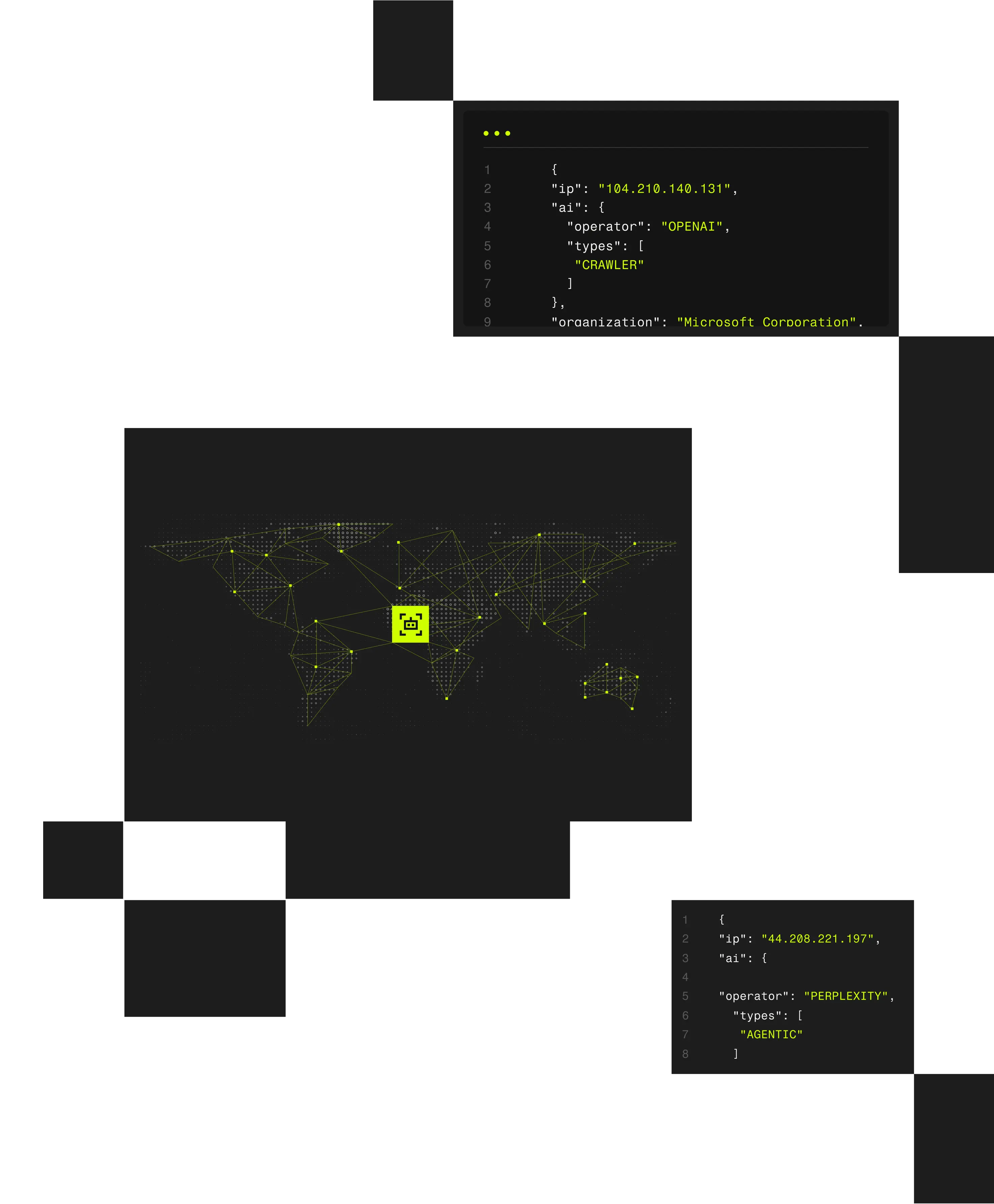
Remote worker fraud occurs when malicious actors pose as legitimate employees or contractors, using VPNs, proxies, and location spoofing to misrepresent where they are actually working from. Spur exposes both the infrastructure and geographic context behind remote access to identify deception before trust is established.


Fraudulent Workers Blend Into Legitimate Remote Teams.
Remote hiring and distributed workforces have expanded access to sensitive systems across locations organizations can’t easily verify. Adversaries exploit this shift by applying for remote roles and using VPNs, proxies, and manipulated location signals to conceal their true point of presence.
Traditional identity and access controls struggle to detect this deception once access appears legitimate. Spur combines infrastructure-aware IP intelligence with validated geolocation to help organizations detect fraudulent remote workers early and continuously.

How Spur Uncovers Deception In Remote Work Environments.
Spur delivers infrastructure-aware IP intelligence and validated geolocation that help security, identity, and risk teams detect fraudulent remote workers, validate access claims, and prevent deceptive actors from gaining or maintaining trusted access.
Astrill VPN and DPRK Remote Worker Fraud
Spur’s research examines how malicious actors pose as legitimate remote workers by using commercial VPN services and anonymized infrastructure to conceal their true location and affiliations.
The analysis highlights real-world cases involving fraudulent IT workers and demonstrates how infrastructure-aware IP intelligence and validated geolocation can expose deception that traditional identity and access controls miss.
Evidence You Can Act On.
Spur’s verified IP intelligence helps teams move faster, detect more, and protect what matters – without adding friction for real users.
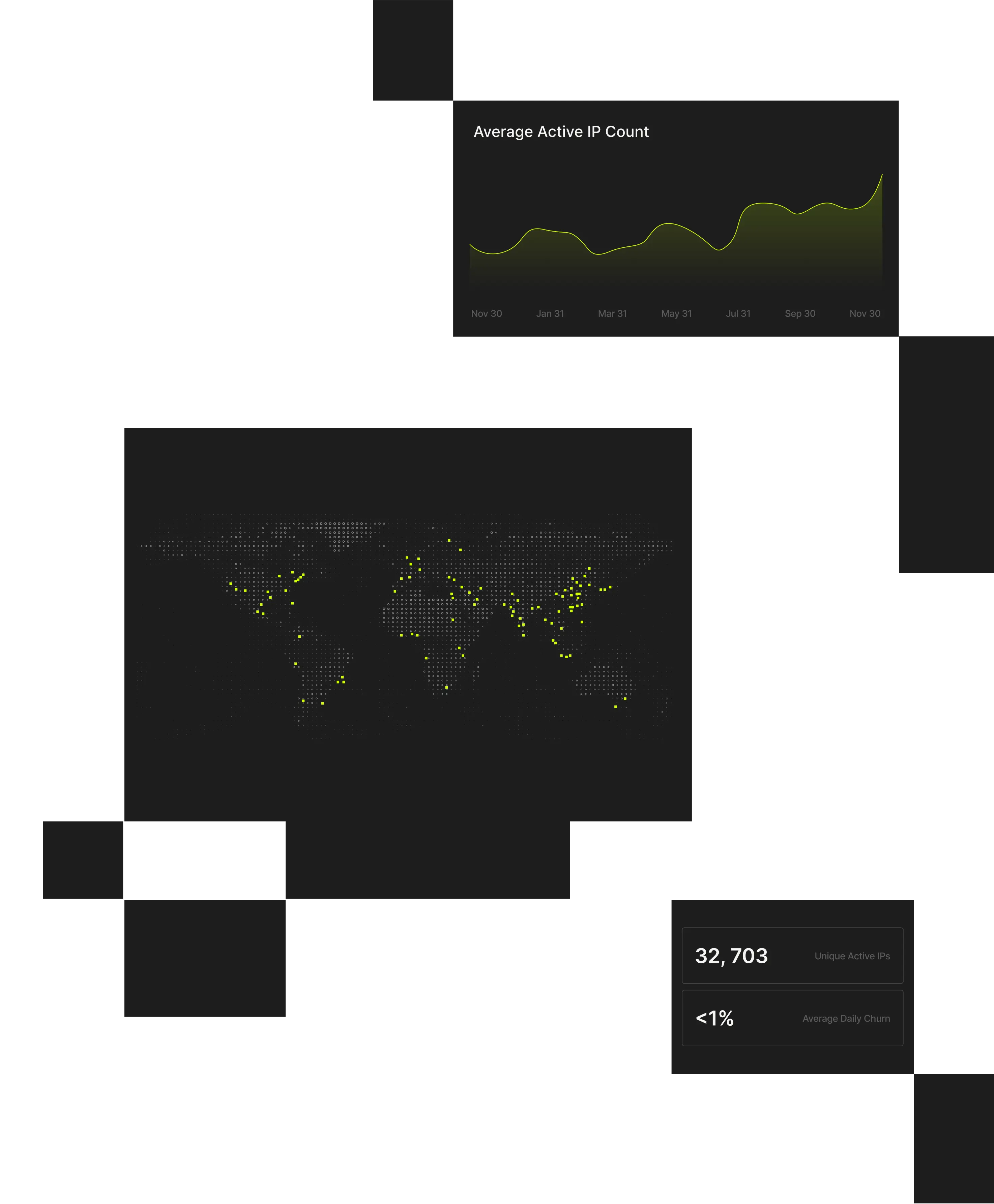
230M+
Unique anonymized IPs detected every 90 days, distilled into 60M suspect IPs daily
1000+
VPN and proxy services detected
20+
Enrichment attributes for full context (geo, ASN, proxy type, device, tunnel entry/exit, etc.)
Where Spur Strengthens Every Layer of Defense.
Uncover Deception in Remote Work.
Identify fraudulent job applicants and deceptive remote access by exposing anonymized infrastructure and validated geographic context.