VPN Detection.
Identify VPN and proxy traffic across security, fraud, and threat hunting workflows.
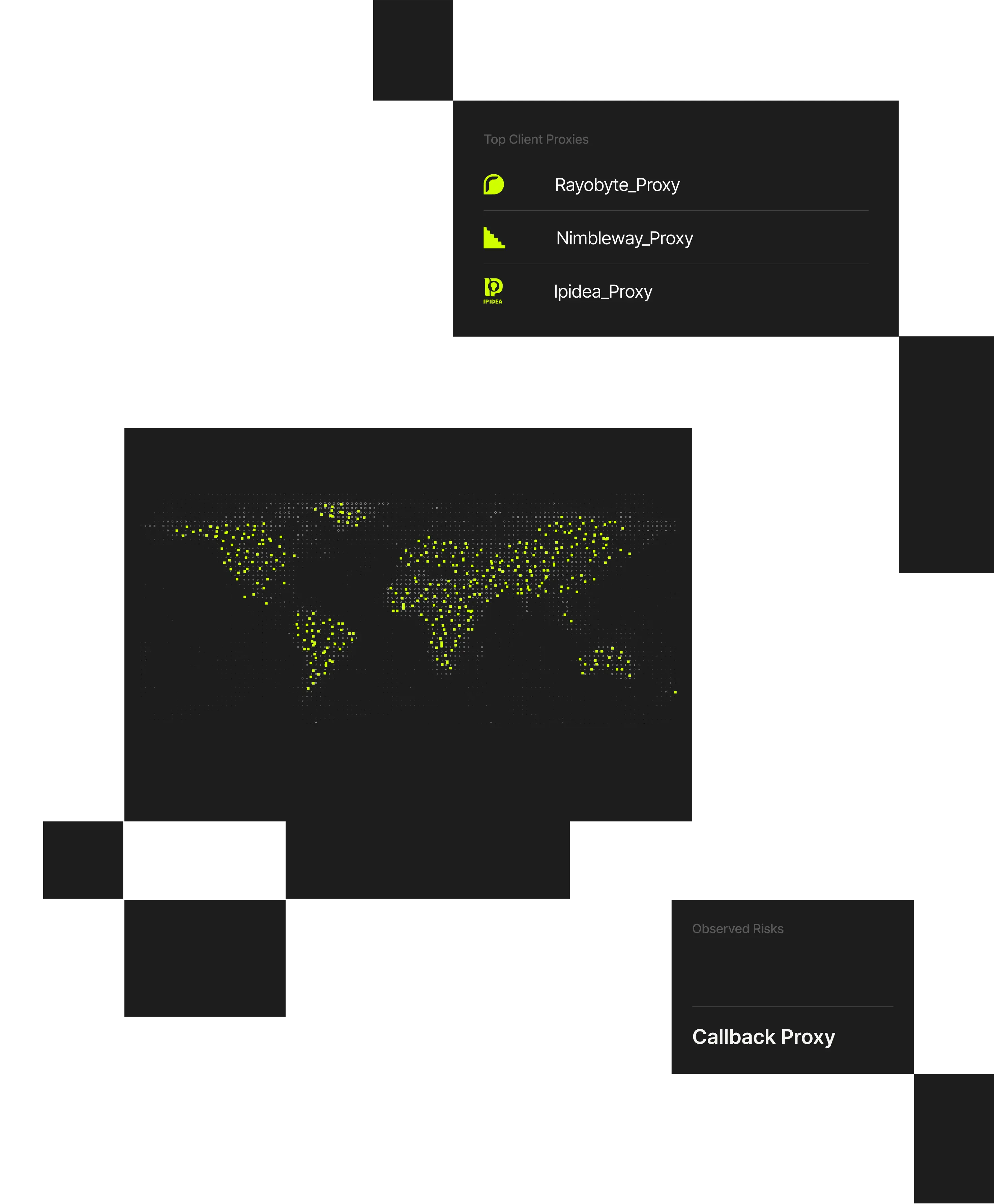
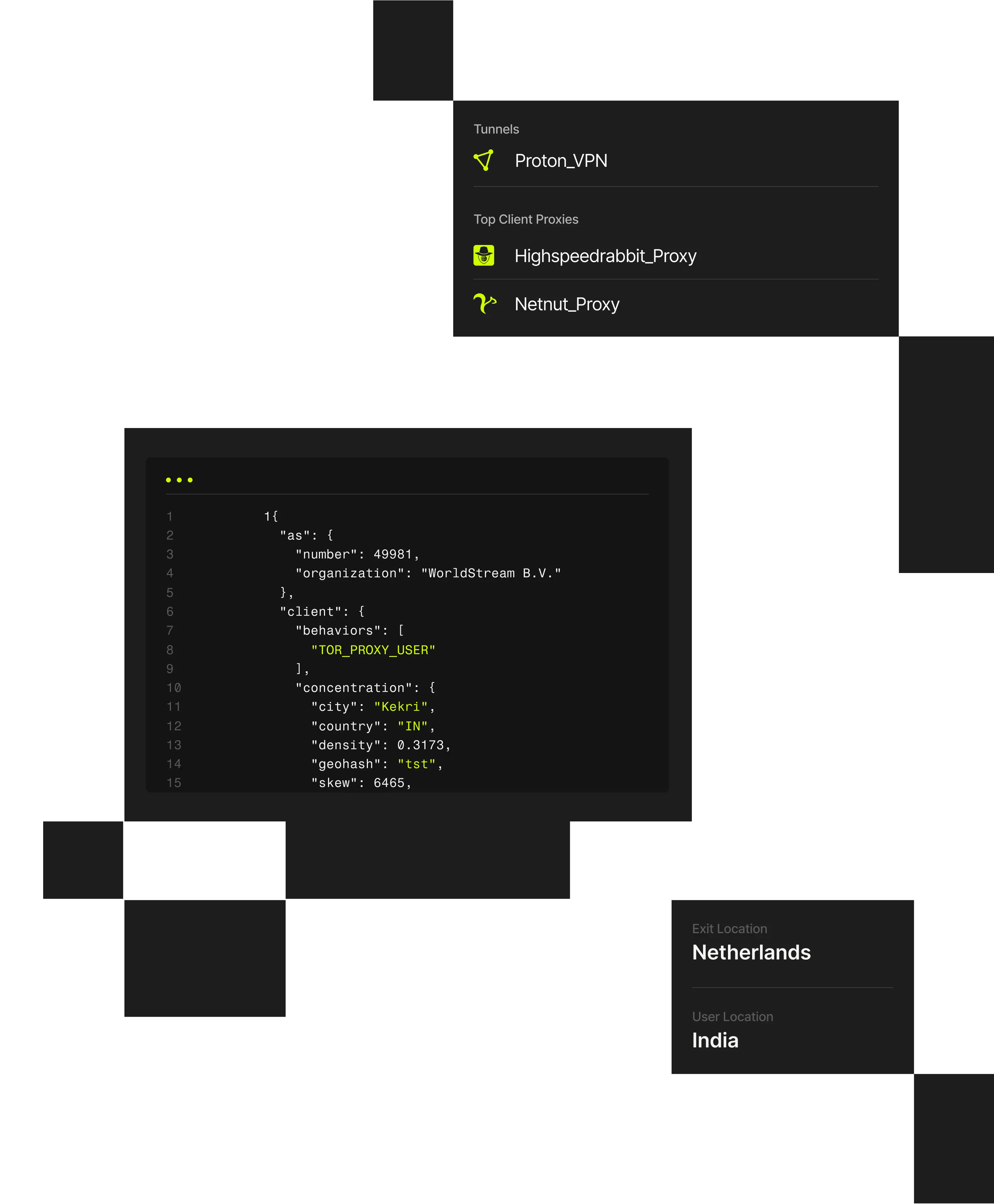
Spur VPN Detection classifies anonymized infrastructure in real time, revealing traffic originating from commercial VPNs, datacenter proxies, or shared gateways.
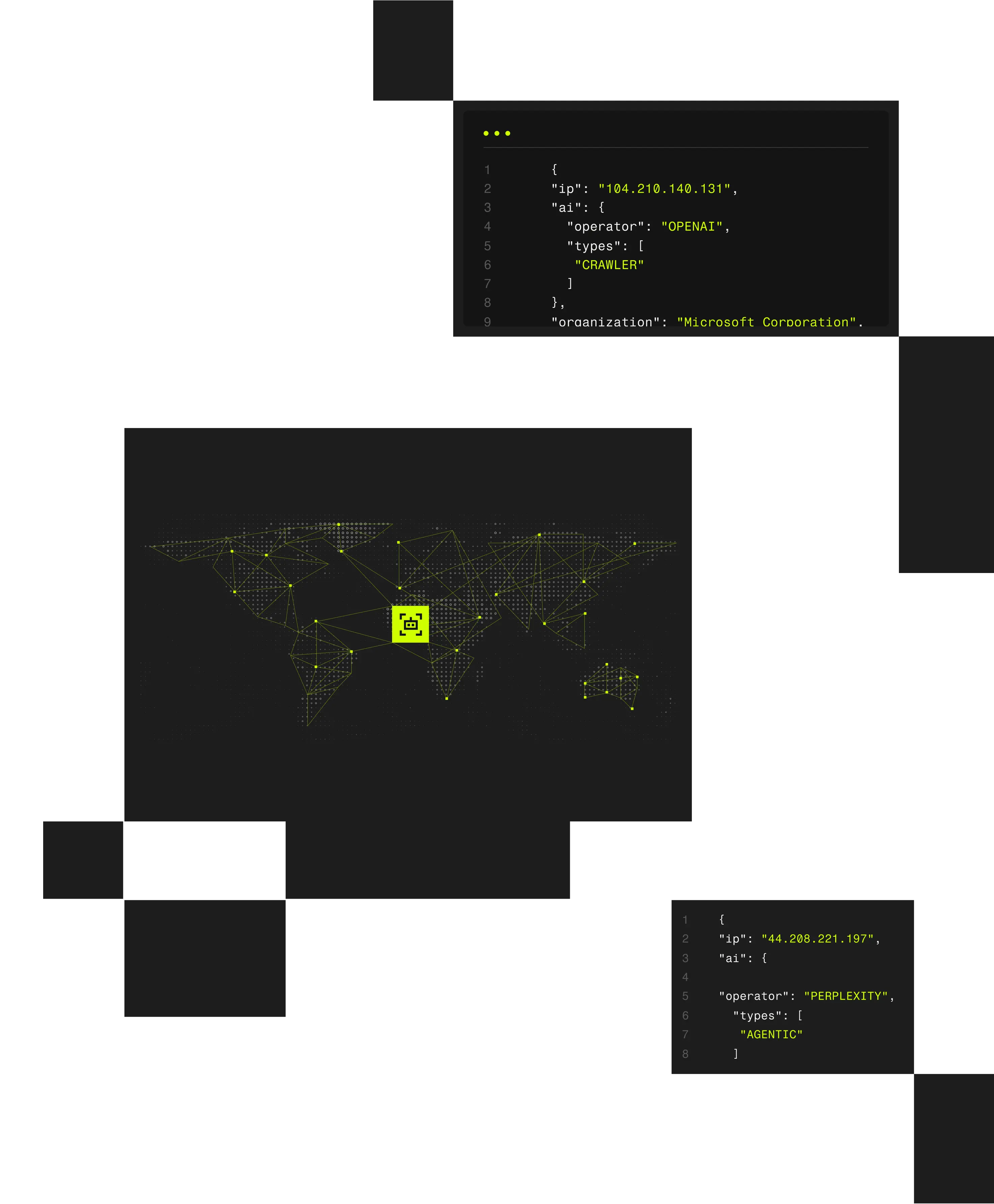
The Spur platform maps and attributes VPN and proxy infrastructure in real time. It analyzes network telemetry, tunnel behavior, and ASN routing to identify anonymized services across hundreds of millions of IPs and 1,000+ VPN and proxy providers.
Spur’s verified, explainable data helps teams distinguish legitimate enterprise VPN use from anonymized traffic used for abuse, without relying on static reputation lists or black-box scoring.
Key Benefits:
- Identify VPN and proxy use in authentication and access workflows.
- Enforce policies with verified, explainable signals instead of static IP lists.
- Strengthen fraud and compliance decisions while minimizing false positives.

How Spur Detects and Classifies VPN Traffic.
- 01
Identify:
- 02
Correlate:
- 03
Enrich:
Why Teams Choose Spur VPN Detection.
Signals that Drive Accurate Detection.
Spur VPN Detection leverages multiple independent signal categories to ensure accuracy and explainability:
Where Spur VPN Detection Delivers Value
Trusted by Teams Who Need to See What’s Real.
- Read Case Study
Technology Company:
Reduced fraudulent sign-ups by 90%+, blocking VPN-origin account creation traffic.
- Read Case Study
Financial Services:
Reduced successful account takeovers by 40%+ by flagging anonymized VPN logins.
- Read Case Study
Gaming Company:
Identified 92% of anonymized VPN traffic to prevent abuse and evasion.
FAQs About Spur VPN Detection.
Identify VPN Traffic Others Miss.
Enrich security, fraud, and threat hunting workflows with verified, explainable IP intelligence.