Enhance Perimeter Security. Expose Hidden Threats at the Edge.
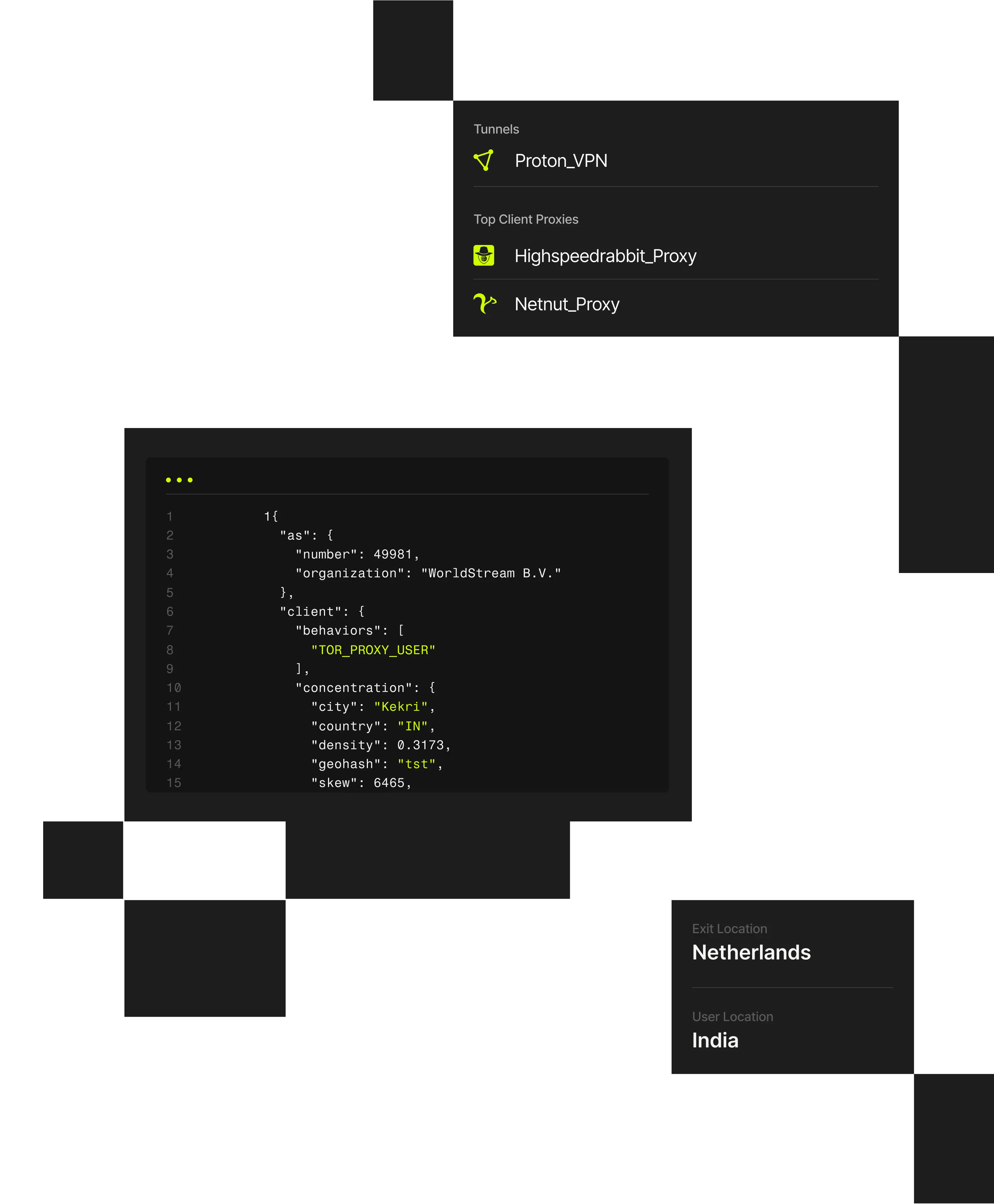
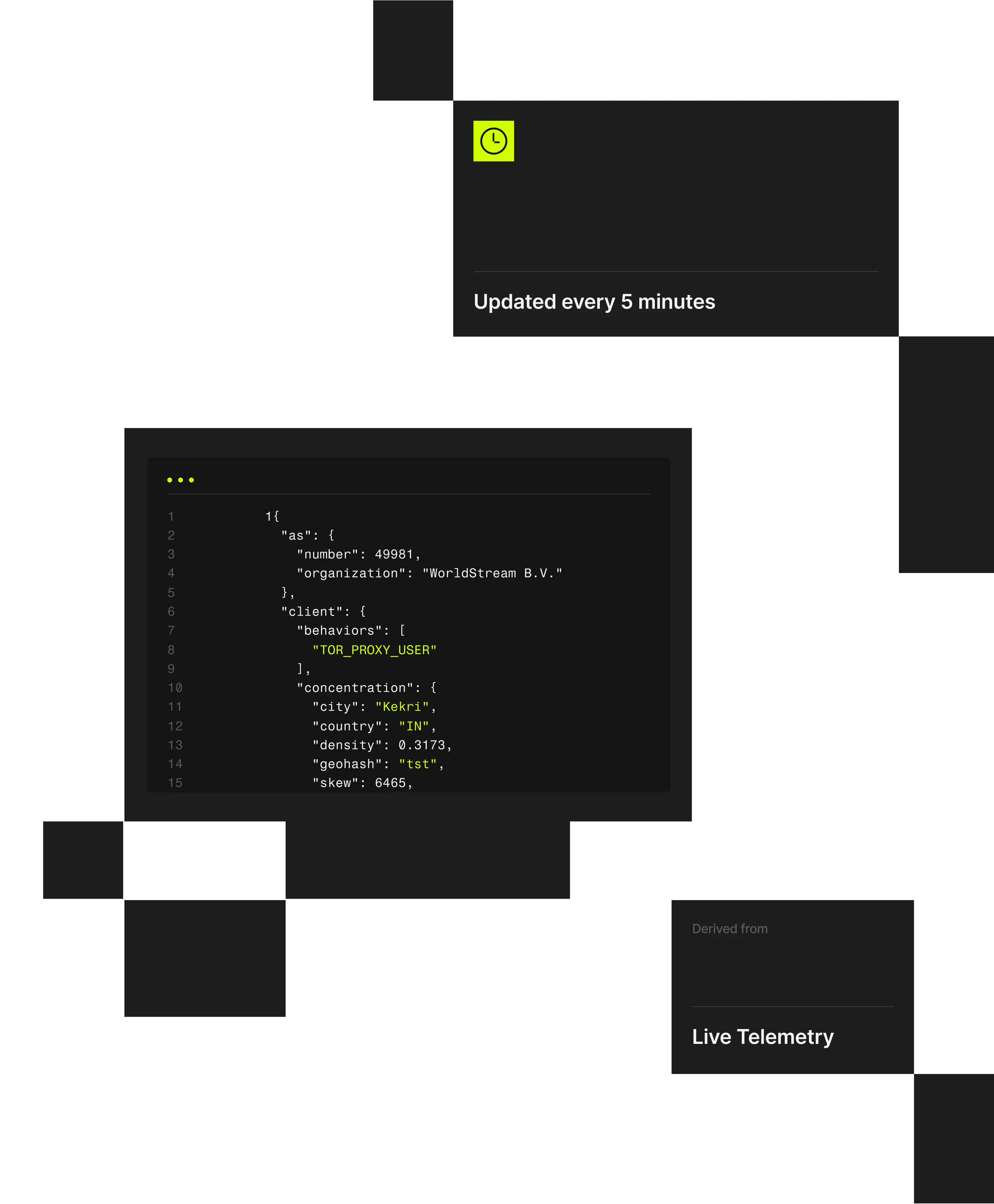
1 "client": {2 "city": "Weldon Springs"3 "behaviors": ["TOR_PROXY_USER"],4 "concentration": {5 "country": "US",6 "density": 0.202,7 "geohash": "9yz",8 "skew": 45,9 "state": "Missouri",
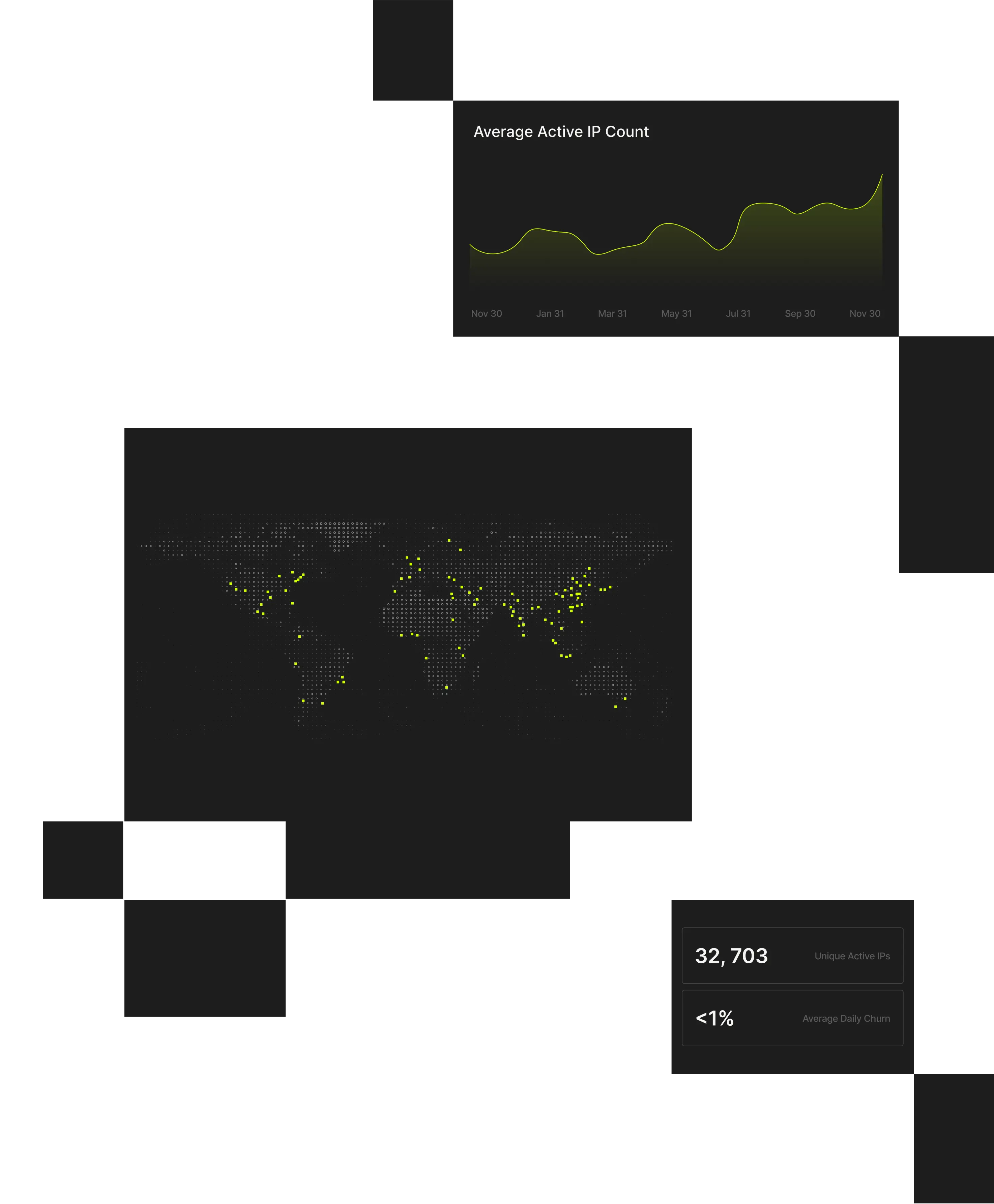
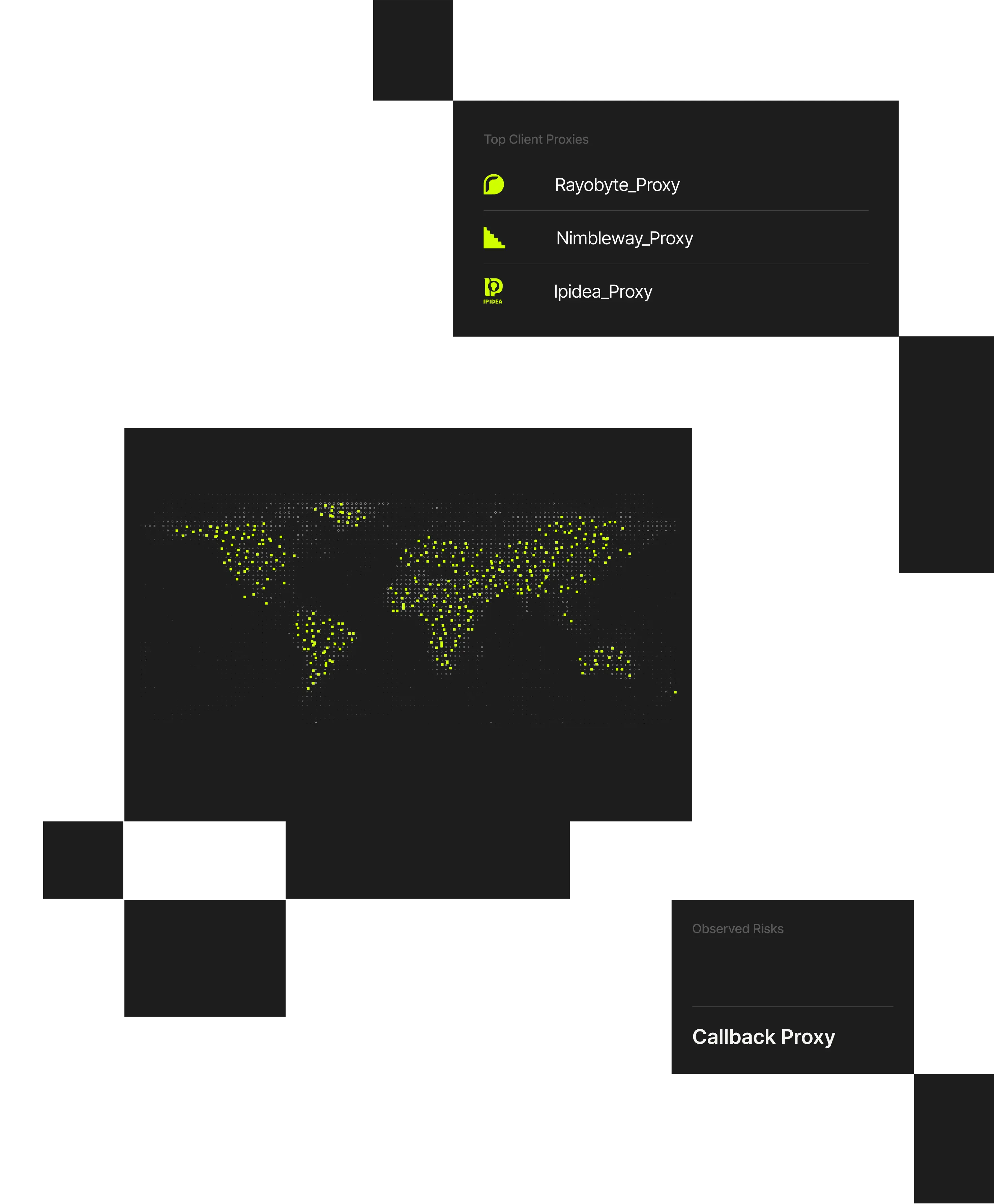
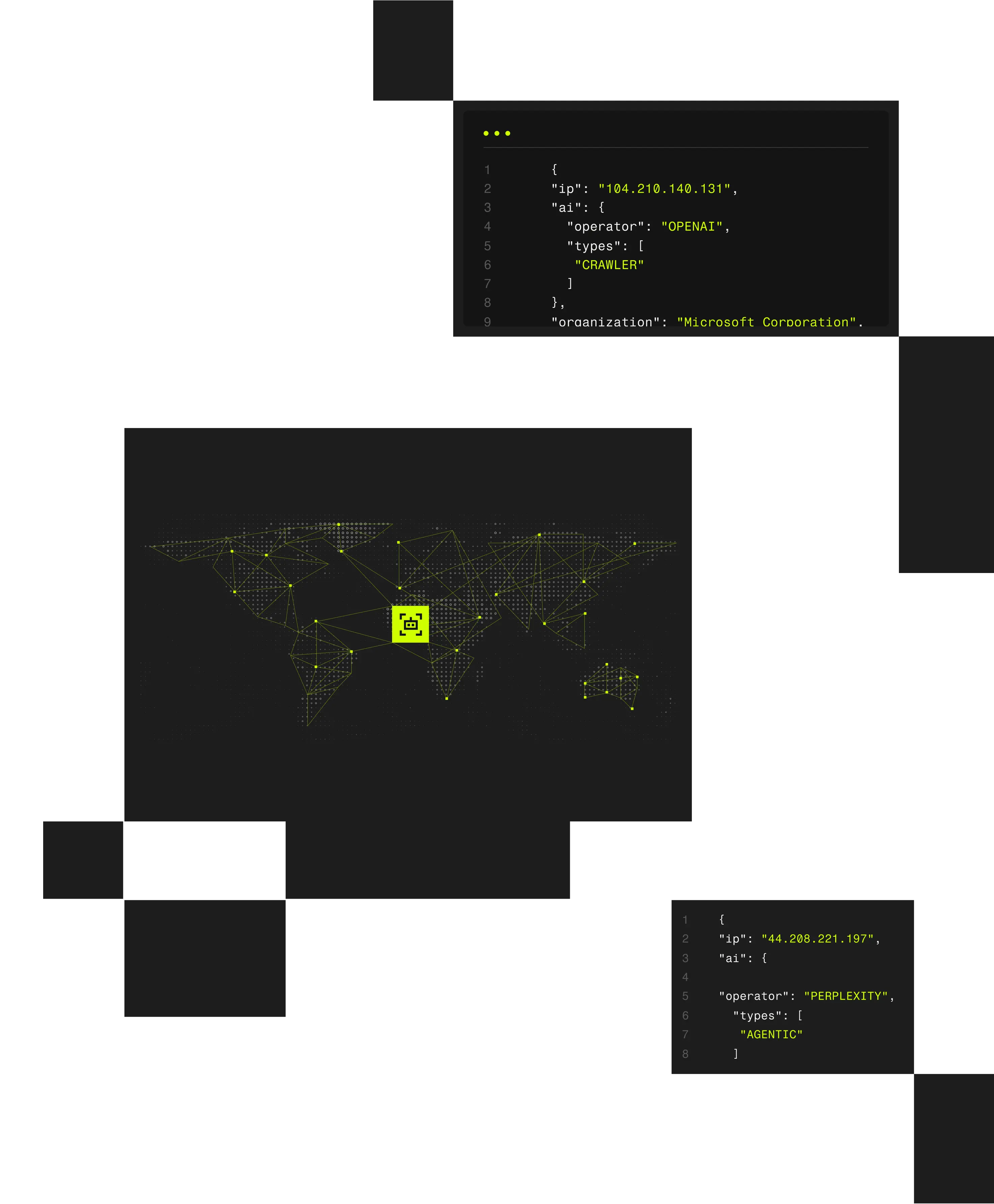
Perimeter threats are driven by attackers using VPNs, residential proxies, and anonymized infrastructure to disguise scanning and intrusion attempts as legitimate traffic. Spur reveals the infrastructure behind inbound connections so teams can control masked threats at the edge.


Malicious Access Blends Into Normal Inbound Traffic
Modern enterprises face an expanding attack surface driven by cloud adoption, hybrid work, and third-party integrations. Attackers leverage anonymized infrastructure to probe environments, bypass access controls, and persist without triggering traditional alerts.
Spur’s verified IP enrichment exposes these hidden connections, enabling security teams to strengthen perimeter monitoring, validate access, assess risk, and protect platform integrity.

How Spur Strengthens Perimeter Defense.
Spur delivers infrastructure-level visibility that helps security teams detect masked threats, apply targeted edge controls, and reduce blind spots at the perimeter.
Ecommerce Platform Blocks Automated Abuse at the Perimeter
GoPuff reduced automated abuse targeting its ecommerce platform by identifying bot traffic routed through residential proxies and anonymized infrastructure.
By applying targeted controls at the perimeter, GoPuff was able to protect site performance and availability during high-demand periods without disrupting legitimate customers.
Evidence You Can Act On.
Spur’s verified IP intelligence helps teams move faster, detect more, and protect what matters – without adding friction for real users.
230M+
Unique anonymized IPs detected every 90 days, distilled into 60M suspect IPs daily
1000+
VPN and proxy services detected
20+
Enrichment attributes for full context (geo, ASN, proxy type, device, tunnel entry/exit, etc.)
Where Spur Strengthens Every Layer of Defense.
See What’s Hiding at the Edge.
Detect masked reconnaissance, anonymized access, and coordinated threats at the perimeter with verified, explainable IP enrichment.